Solving MalwareTech’s RE Challenges: Strings
I’ve been wanting to post write-ups about different CTF’s and challenges that I have done, and I’m finally getting round to doing it. And as I’ve been recommended to use Cutter when performing Static Analysis, I decided to kick of the challenge section with some of MalwareTech’s static RE challenges, which you can find here. In this part, we’ll be working through the strings challenges, as they’re quite short and simple. So let’s begin!
As it says on the site, “all challenges are designed to be completed without using a debugger. Your goal should be to be able to complete each challenge without running the exe“, and it is all possible in the free version of IDA Pro – so let’s use Cutter, a GUI of that-quite-complex-CLI-dissassembler radare2. Cutter was developed for those who didn’t like the command line interface of r2 (like me), and preferred to use tools like IDA for the simplicity. I’ll be installing and using it on Ubuntu, however it also works on Windows and OSX.
You will definitely need r2 in order to use Cutter, so let’s install that first – although if you are using the AppImage it comes bundled alongside, saving you time. Otherwise, Simply run
git clone https://github.com/radare/radare2.git cd radare2 ./sys/install.sh
Then it is time to install Cutter. Go here, and download the latest App image for Linux, Windows or OSX – or you can go here to find out how to build from source. So, now we can get started with the reversing!
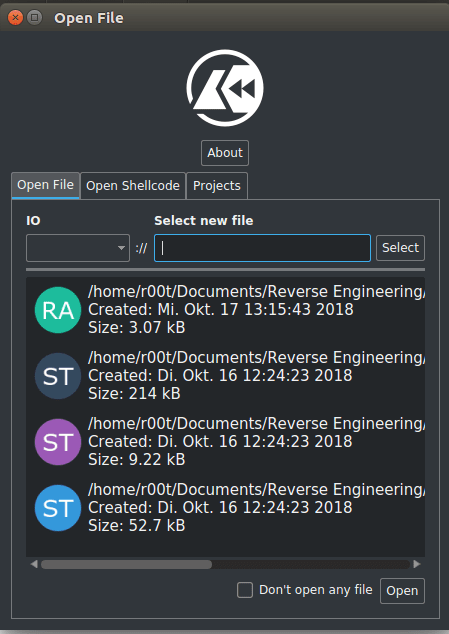
Once you’ve downloaded the 3 string challenges, open up Cutter and select strings1.exe_ and click Open. You can ignore the next section for these challenges – it isn’t necessary, so simply hit Ok. It will load the binary and display the assembly of the file.
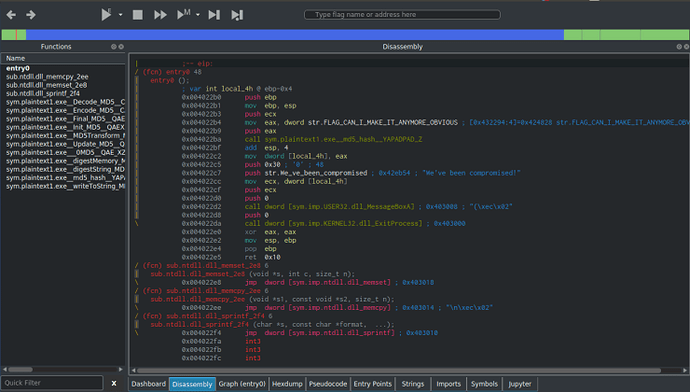
It doesn’t take a genius to work out their way around Cutter, but for the complete beginners to reversing, here are the important bits.
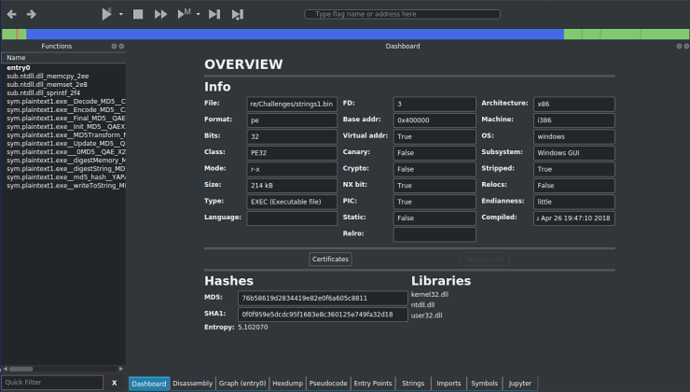
The Dashboard gives you an overview of the file itself – the file format, the architecture of the file, base address, all that good stuff. It also shows you the libraries used and the MD5 and SHA1 hashes of the binary, as well as the Entropy.
The Dissassembly, as the name suggests, shows the assembly code for the executable, which is 32 bit in this case.
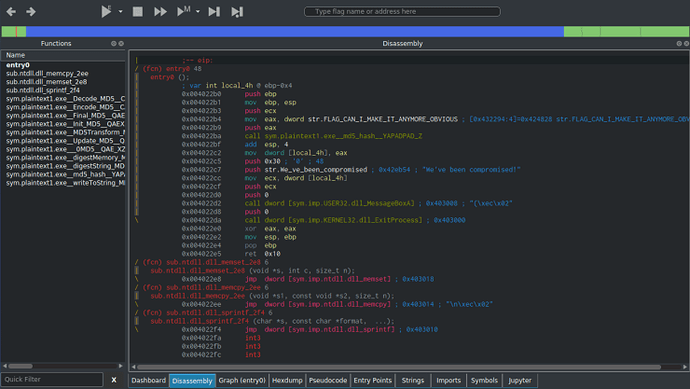
The Graph shows the flow of the program in a more simpler way than the regular dissassembler window, so you can follow the flow easier.
The Hexdump is pretty much a hex editor.
Strings show the strings inside of the program.
And finally, Pseudocode displays the assembly in a higher level “language” similar to C, allowing you to understand what is happening in the code without delving too deep into the assembly.
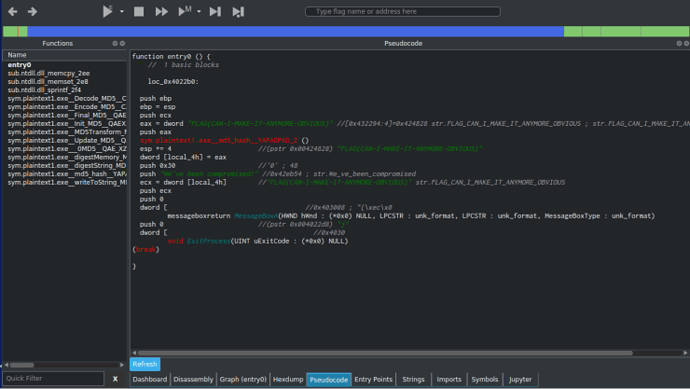
With that all in mind, let’s jump back to the Graph view and try and see what is happening. The first function call is taking 3 arguments, with one of them being FLAG_CAN_I_MAKE_IT_ANYMORE_OBVIOUS which is located at 0x424828. We should check it out.
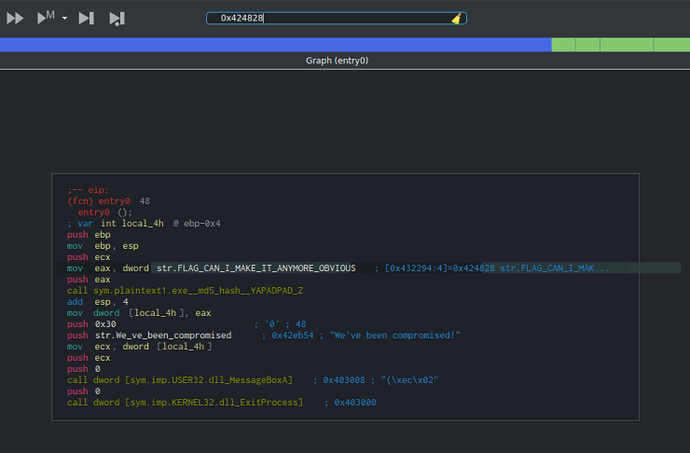
At the top of the window, there is an input box that allows you to input an address, so input the value 0x424828, and hit enter. Sure enough, there is the suspected flag:
FLAG{CAN-I-MAKE-IT-ANYMORE-OBVIOUS}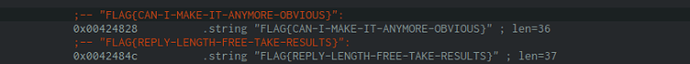
To check it, go here and enter the flag in the box at the bottom.
If the flag is correct, the website should show Correct Flag! otherwise it will display Incorrect, try again! Now the first challenge is done, let’s move onto strings2.exe_!
Once again, open it up with Cutter and open the Graph window. Almost immediately, you can see multiple mov instructions, with hexadecimal values being moved into local variables. Luckily for us, Cutter automatically translates these into regular characters, so we can view the flag without having to look into the code whatsoever:
FLAG{STACK-STRINGS-ARE-BEST-STRINGS}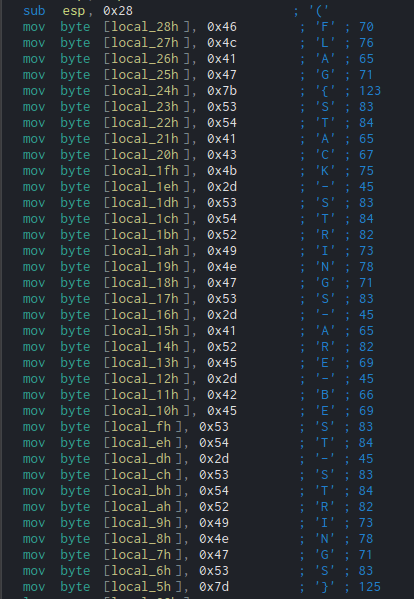
Check it here and it should show Correct Flag! We can now move onto the final, slightly more difficult challenge – strings3.exe_.
For this one, it is much easier to do on Windows as I will be using a Windows executable, otherwise, you can use Wine like I am. So, opening up the file in Cutter, we can see 2 very interesting API calls which have not been present in either the first or second challenge; FindResourceA and LoadStringA. Based off of these calls, we can guess that the string is kept in the resources. I will be using ResourceHacker in order to view the resources in the file, although Cutter does have an inbuilt resource viewer.
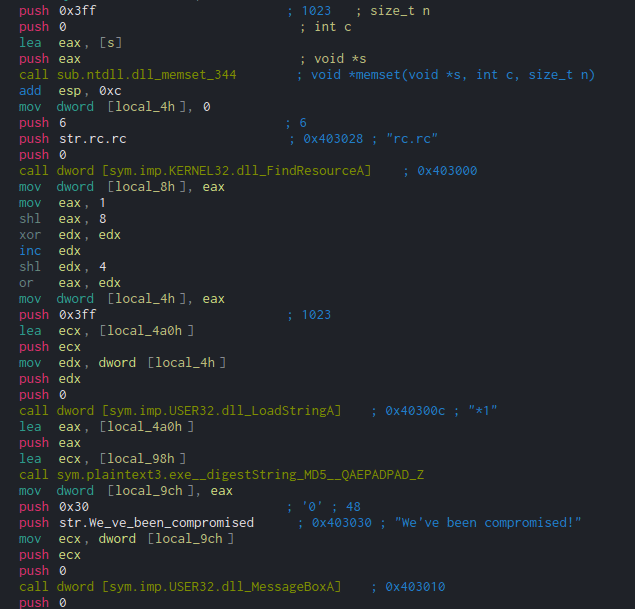
Opening it up in RH, it is clear that there are a lot of possible strings, and there is no point in brute forcing it as that’s cheating. So, let’s work through the two new API calls to identify which string is the correct string.
As always when it comes to reversing anything Windows based, MSDN is your friend. A quick search for FindResource and LoadString yields these results:
HRSRC FindResourceA( HMODULE hModule, LPCSTR lpName, LPCSTR lpType ); int LoadStringA( HINSTANCE hInstance, UINT uID, LPSTR lpBuffer, int cchBufferMax );
The three arguments used in FindResource are 0, “rc.rc” and 6 – this doesn’t really give us much information, so let’s take a look at LoadString, where the four arguments are 0, edx, ecx and 1023.
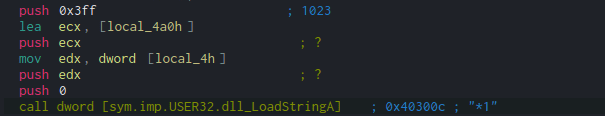
We can see that local_4h (a local variable) is moved into edx just before it is pushed to the stack. Tracing this back, the value (eax) that is moved into local_4h is the result of a Bitwise OR operation between eax and edx. Before this, the registers are used to store numbers, using a mov operation and a shl (Shift Left) operation.
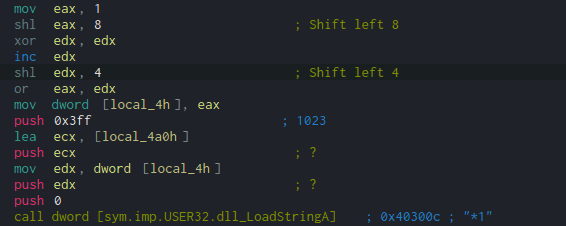
First, eax has the value 1 moved into it, and is then shl‘d by 8. Open up a python interpreter and type 1 << 8. This should result in 256. Then, do the same but with the value 4, so 1 << 4, resulting in 16. Now we have our values, we just need to OR them together.
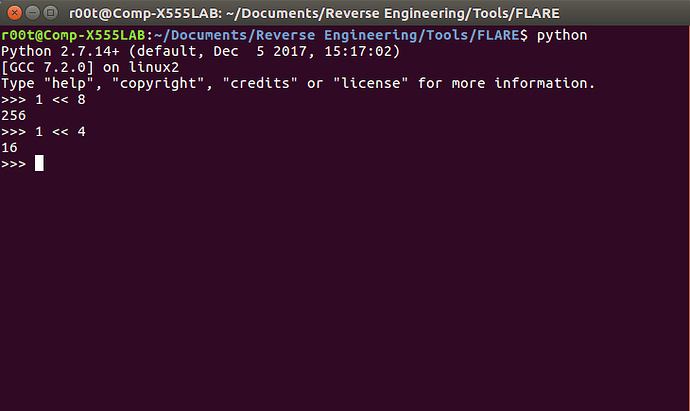
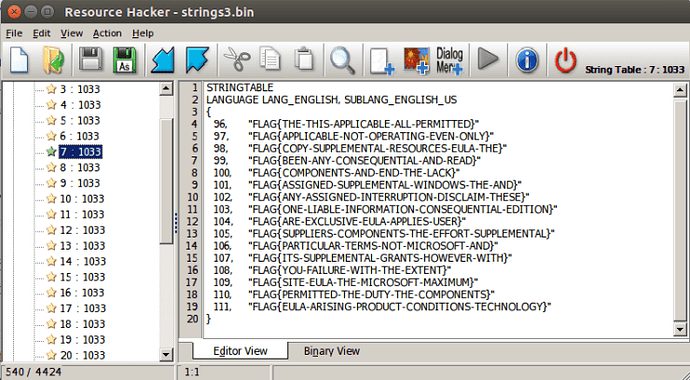
To perform a bitwise OR in Python, simply use this | operator, so you need to type in 256|16, which equals 272. Therefore, the second argument for LoadString is 272, Now, the second argument is identified as the identifier of the string to be loaded. When looking at RH, there were numbers before each of the strings – the identifier. So we need to view the string with the number 272!
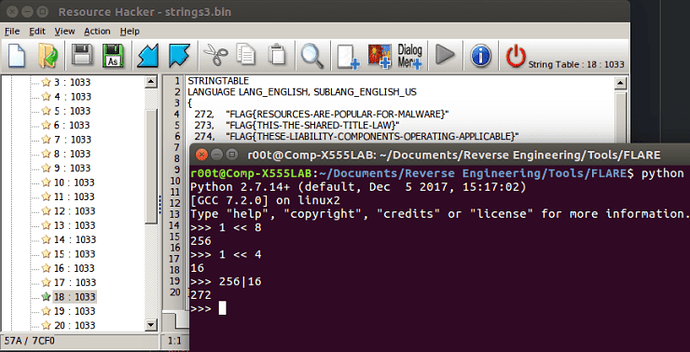
As you can see, the flag is in the 18th string table and the first row:
FLAG{RESOURCES-ARE-POPULAR-FOR-MALWARE}If we check it here, the site should display Correct Flag!, otherwise you have gone wrong somewhere 🙁
Well that is all 3 string challenges finished, so I hope you managed to pick something up from that, and I plan to get through some more of these challenges – as well as write up the Flareon challenges I succeeded in completing, for those starting off in reversing (not just malware analysis). If you want to check out some more advanced tutorials/write ups, check out Megabeets site where he examines and reverse engineers malware, CTF’s and even a Gameboy ROM, all using Radare2 and/or Cutter! Thanks!

