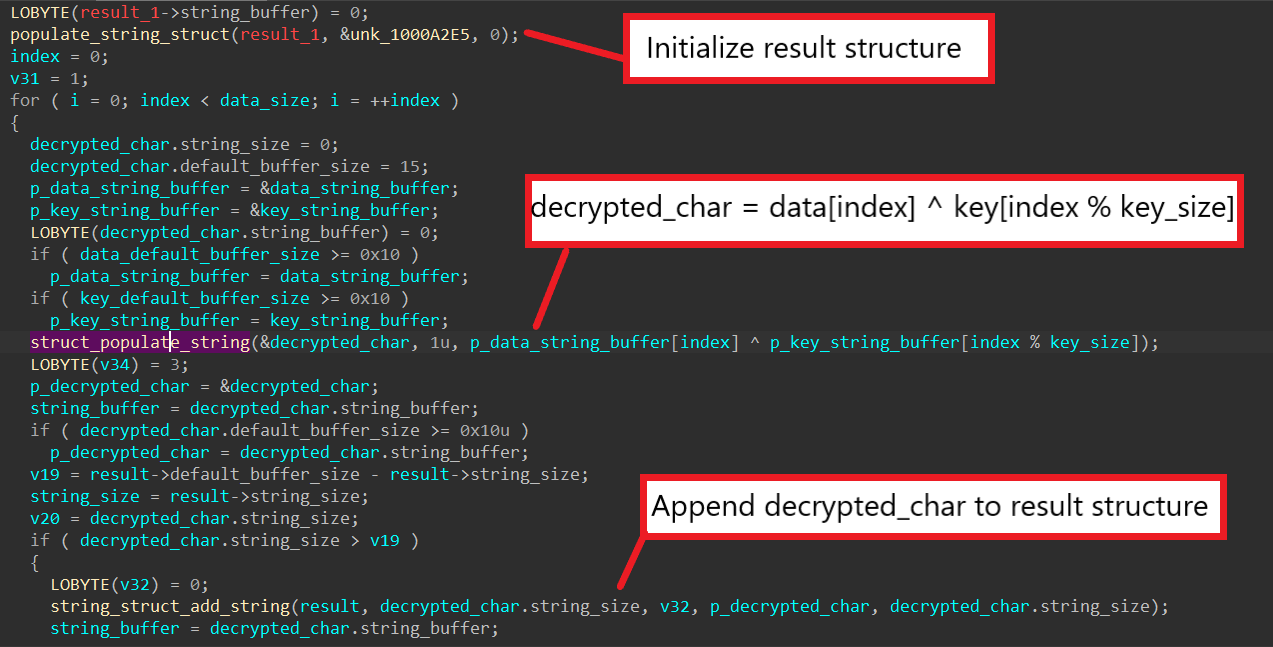
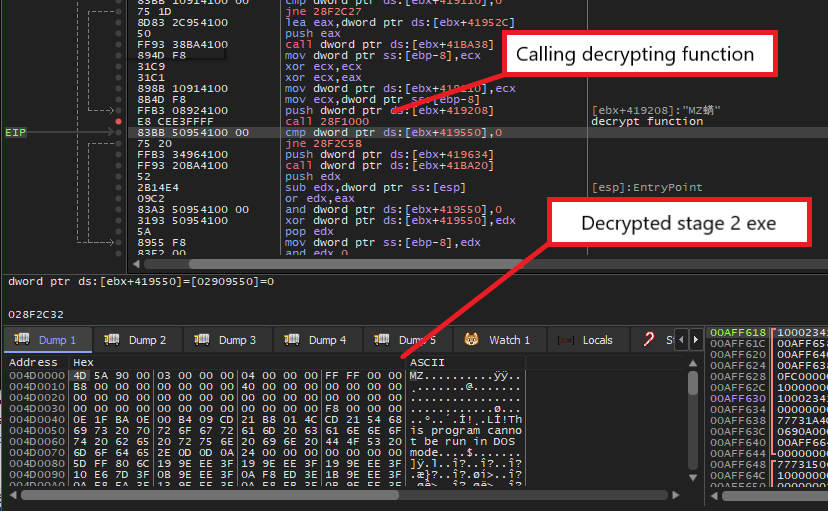
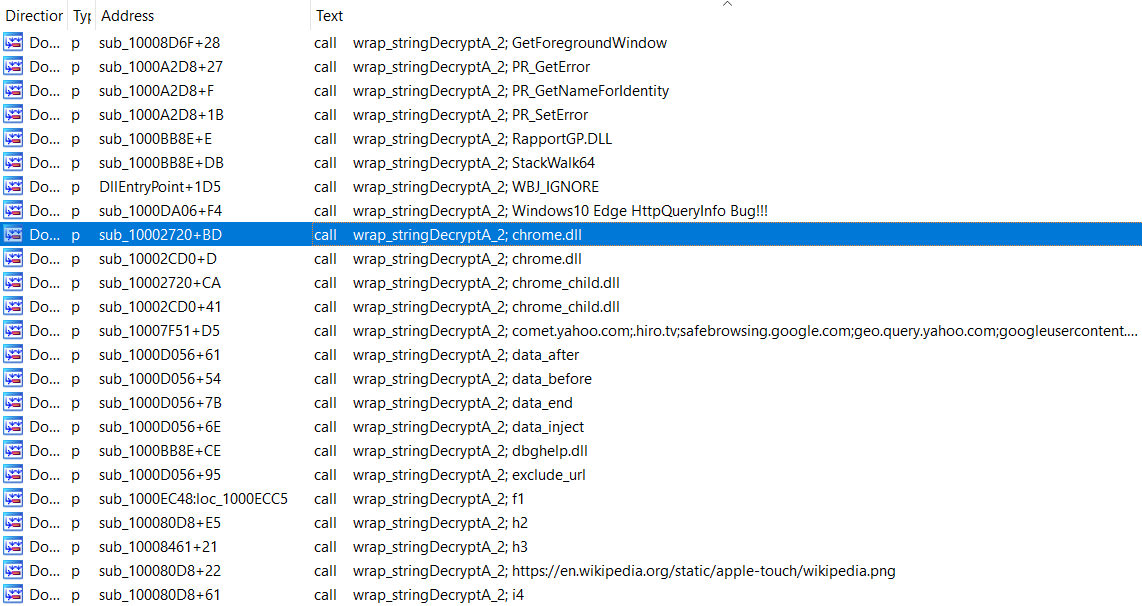
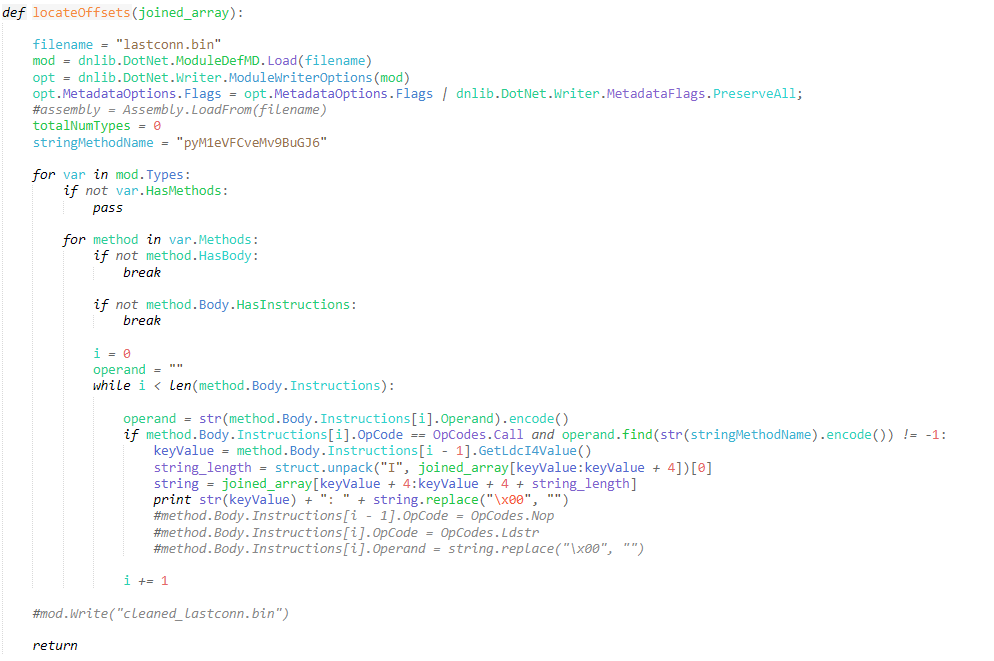
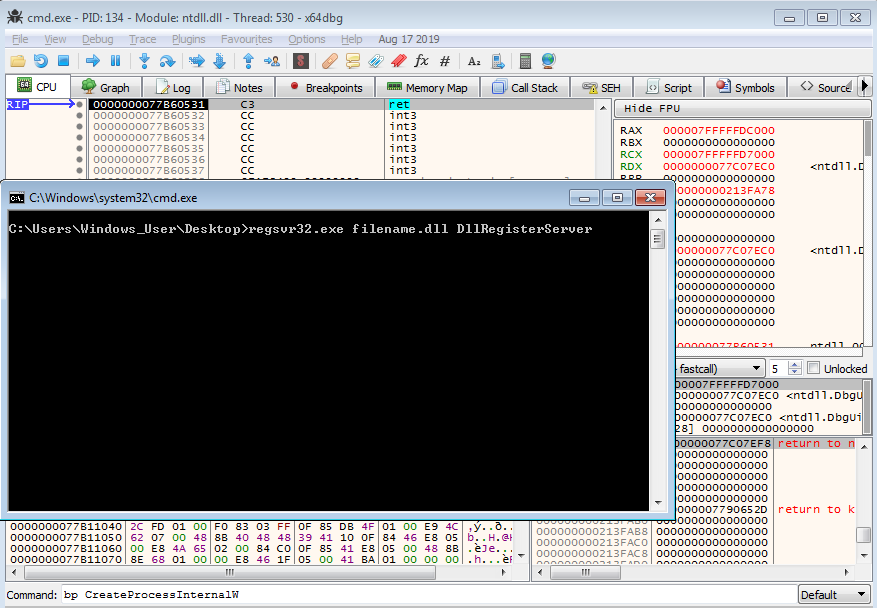
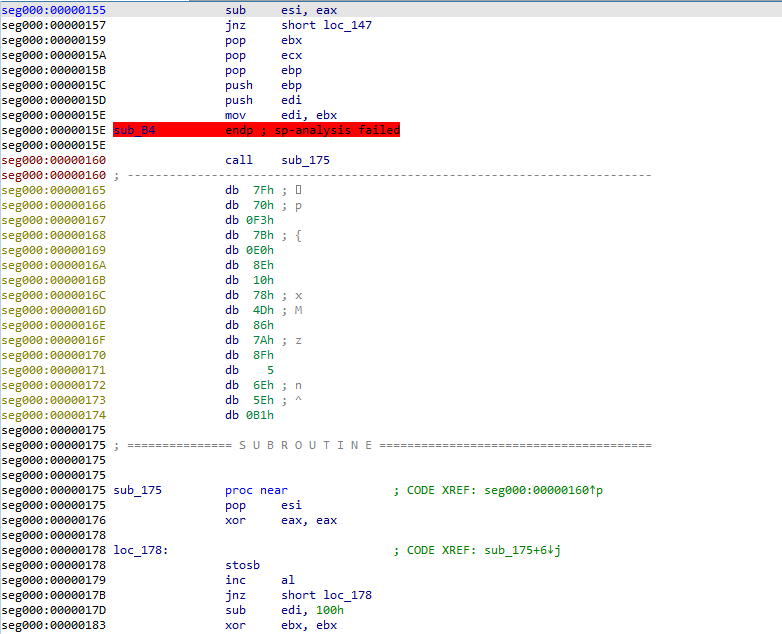
This is a follow up for my last post on unpacking SQUIRRELWAFFLE’s custom packer. In this post, we will take a look at the main loader for this malware family, which is typically used for downloading and launching Cobalt Strike. Since this is going to be a full analysis on this loader, we’ll be covering […]
In the last month, I have heard and seen a lot about SQUIRRELWAFFLE on Twitter, a new loader that has been used in email-based campaigns to download Cobalt Strike or Qakbot to the victim’s machine, so I figure it will be fun to take a look at this new actor! In the initial stage of […]
Qakbot is one of the most notorious malware families currently operating, and dates back to around 2007. It is primarily focused around stealing banking information and user credentials, however with the huge jump in ransomware popularity among threat actors, Qakbot has been seen to drop Egregor and the ProLock ransomware. As it is primarily operated […]
It’s sure been a while since the last post! We’ve gone through several iterations of website design over the past few months (plus fixing all the malformed images due to the theme transfer), but should be back for good now! For this commemorative post, we’ll be diving into a recently discovered malware sample known as […]
So recently I’ve been reverse engineering the newest version of IcedID (the version hiding encrypted payloads and other data inside PNGs), and I came across a post by Malware-Traffic-Analysis about IcedID being downloaded by malspam typically responsible for downloading ISFB. This particular infection chain was interesting, as the Word Document drops a script file to […]
This post is a continuation from my last one, where we reverse engineered the second stage of the shellcode, and replicated the API hashing routine. If you haven’t checked out that post, you can check it out here, and the one before that here! In this post we’re going to be writing an emulator for […]