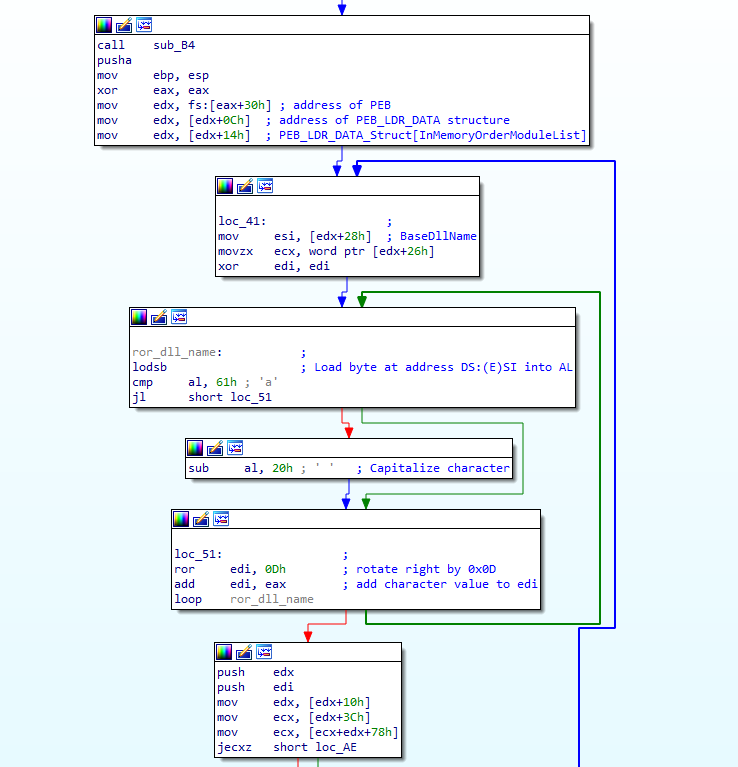
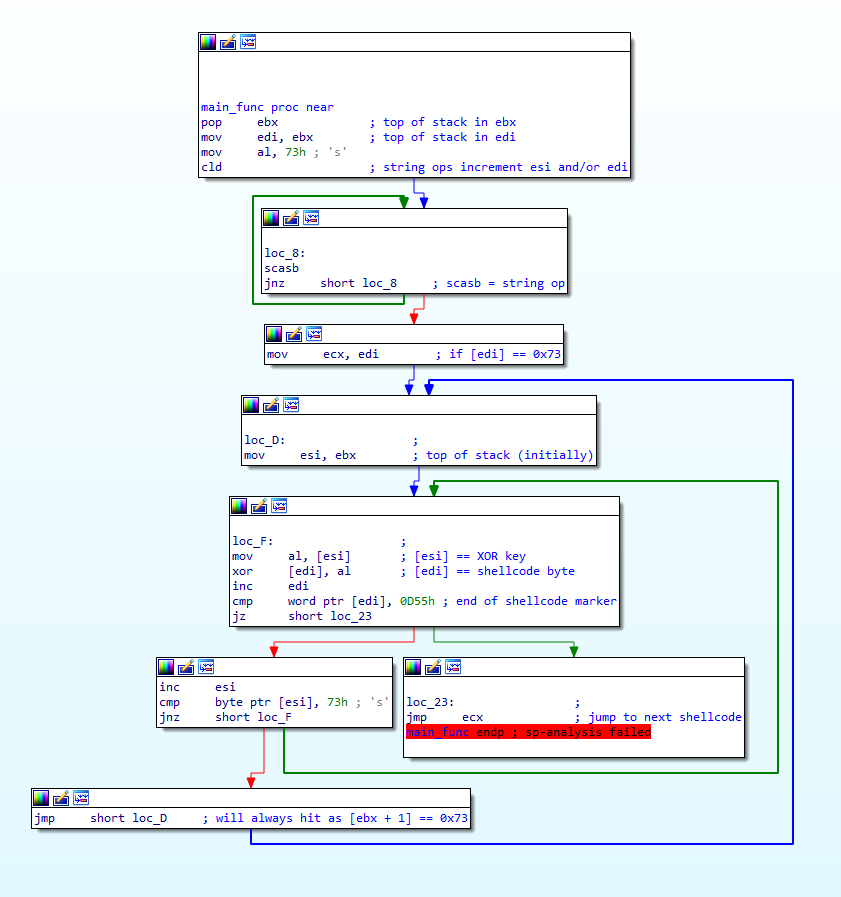
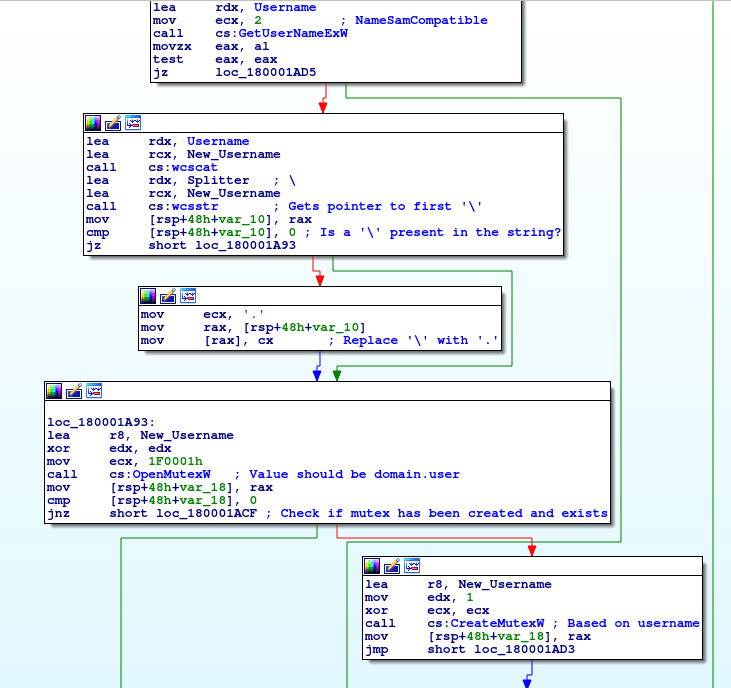
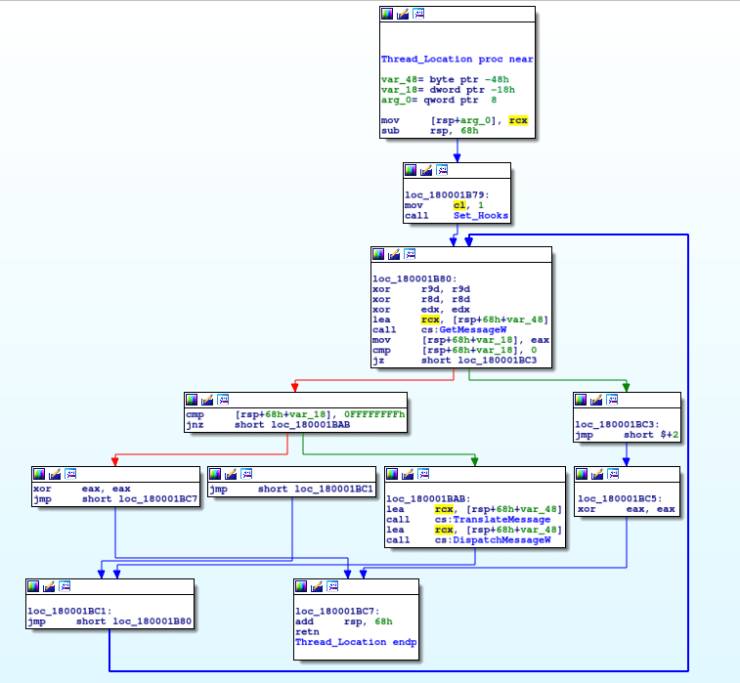
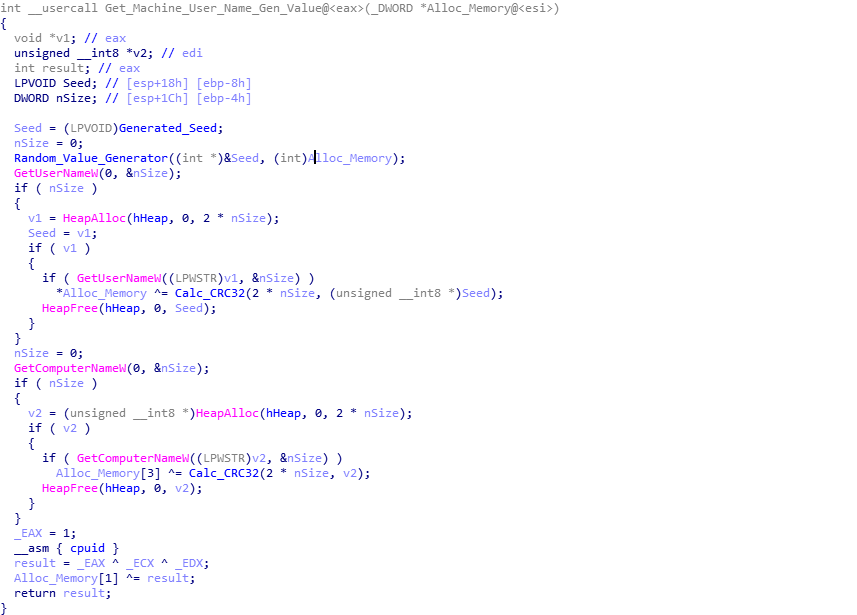
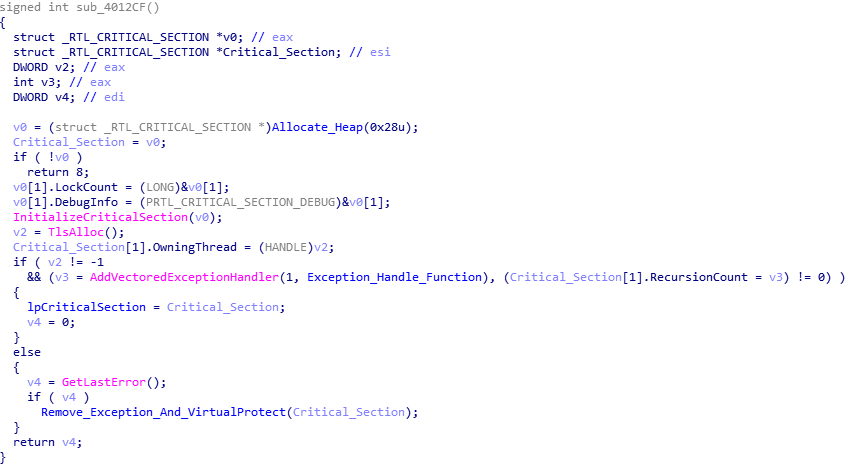
Welcome back! If you haven’t checked out my last post on reverse engineering shellcode techniques, you can check it out here! This time we’re taking a look at stage 2 of the shellcode, which we previously decrypted using IDAPython in the last post. We’re going to be covering quite a lot this week, so if […]
It’s been a while since I posted a blog aimed at beginners in terms of reversing techniques for analyzing malware, rather than a “how-does-it-work” type post, so for this blog post I decided to focus on concepts tied very closely to malicious software, such as shellcode, (recognizing and implementing) encryption algorithms, and so on. I […]
(This post is a reupload from my old site which is no longer available – you may have seen it before) If you haven’t read the first post, go check it out here. You can download this keylogger off of VirusBay. So far we have decrypted a whole lot of text using a simple XOR method, which […]
(This post is a reupload from my old site which is no longer available – you may have seen it before) Whilst I’m working through the Hancitor write up and the Flare On challenges, I decided to take a short break and focus on a smaller piece of malware – such as a keylogger, which […]
So it’s been quite a while since my last post, however now that my Beginner Malware Analysis Course is complete, the posts should be more and more frequent, although that obviously depends on the complexity of the samples I am analyzing. If you haven’t checked out my last post on ISFB where we analyzed the […]
I’m finally getting round to writing this post – for the past few months I have been analysing different versions of ISFB/Ursnif/Gozi to gain a deeper understanding in the functionality of this specific malware. In this post, I will be detailing how to unpack and then analyse the first stage loader executable, and then use […]