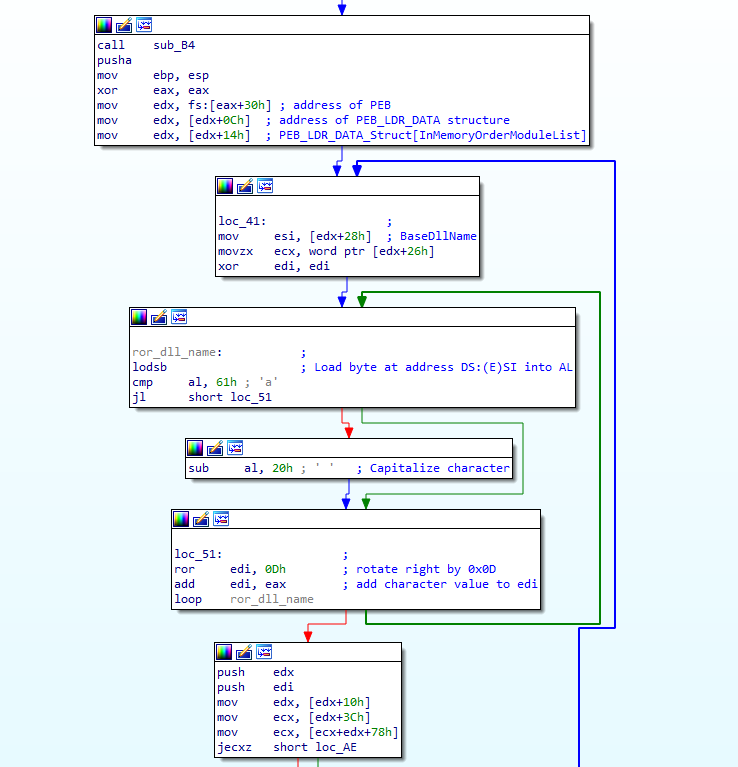
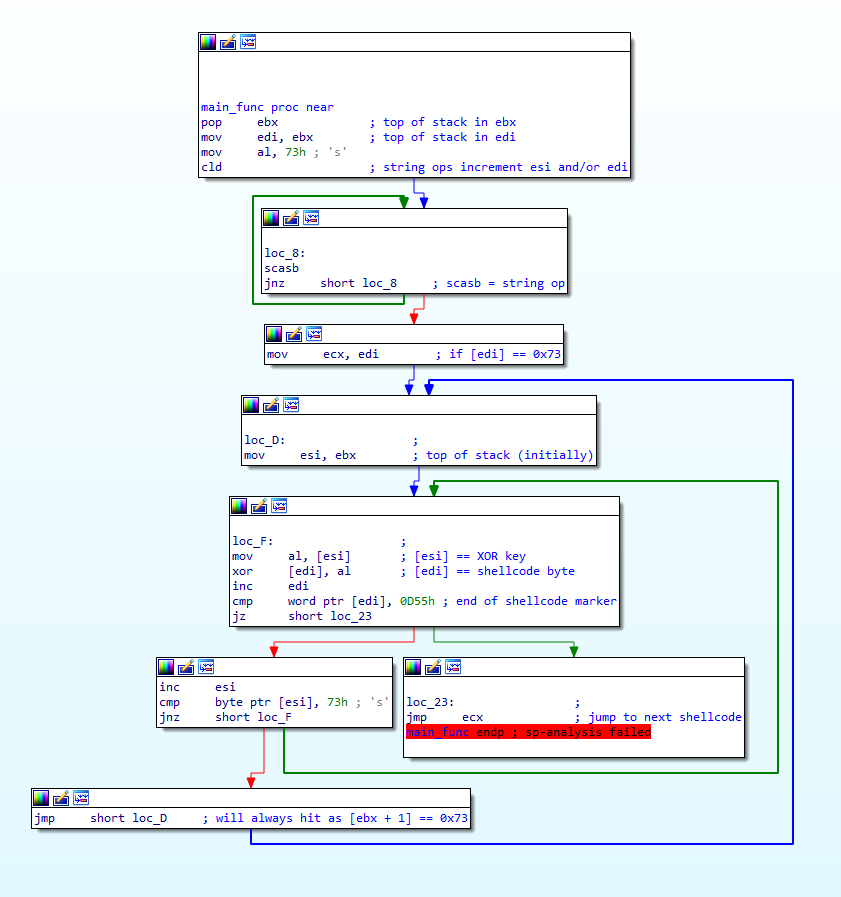
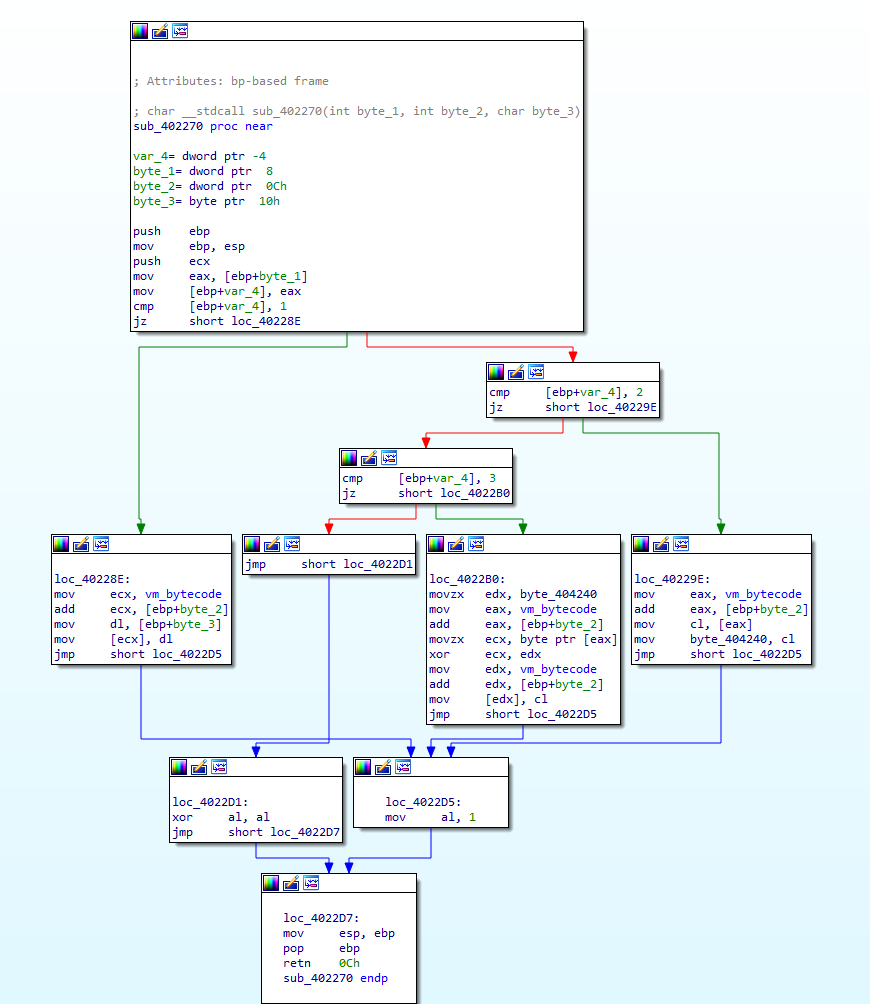
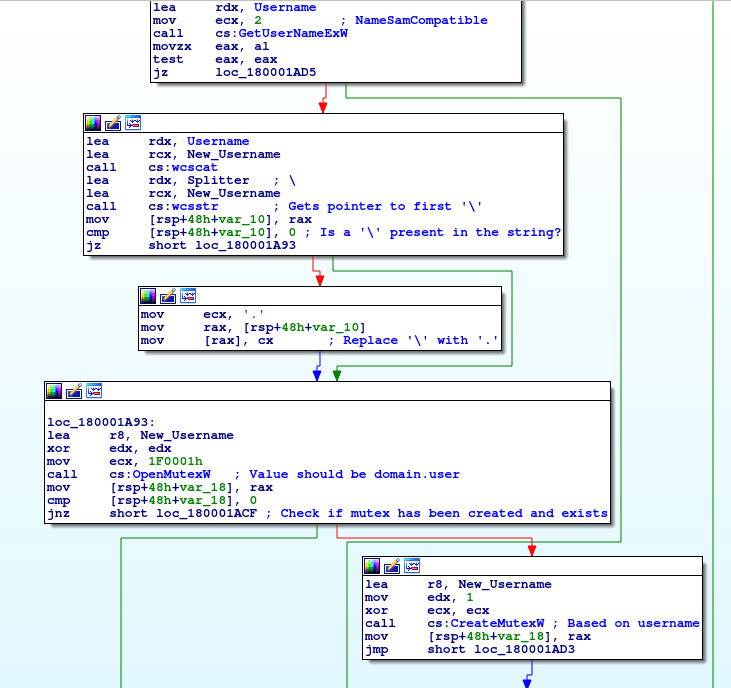
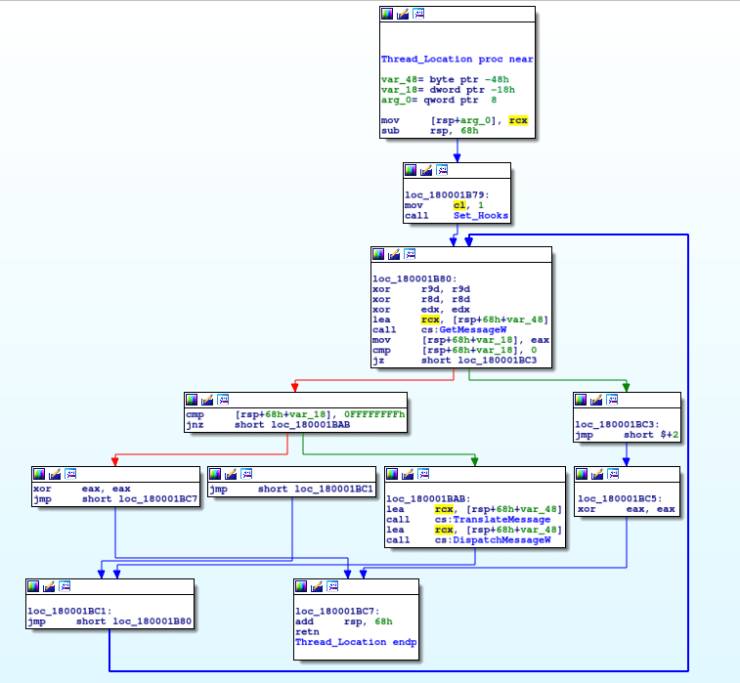
Welcome back! If you haven’t checked out my last post on reverse engineering shellcode techniques, you can check it out here! This time we’re taking a look at stage 2 of the shellcode, which we previously decrypted using IDAPython in the last post. We’re going to be covering quite a lot this week, so if […]
It’s been a while since I posted a blog aimed at beginners in terms of reversing techniques for analyzing malware, rather than a “how-does-it-work” type post, so for this blog post I decided to focus on concepts tied very closely to malicious software, such as shellcode, (recognizing and implementing) encryption algorithms, and so on. I […]
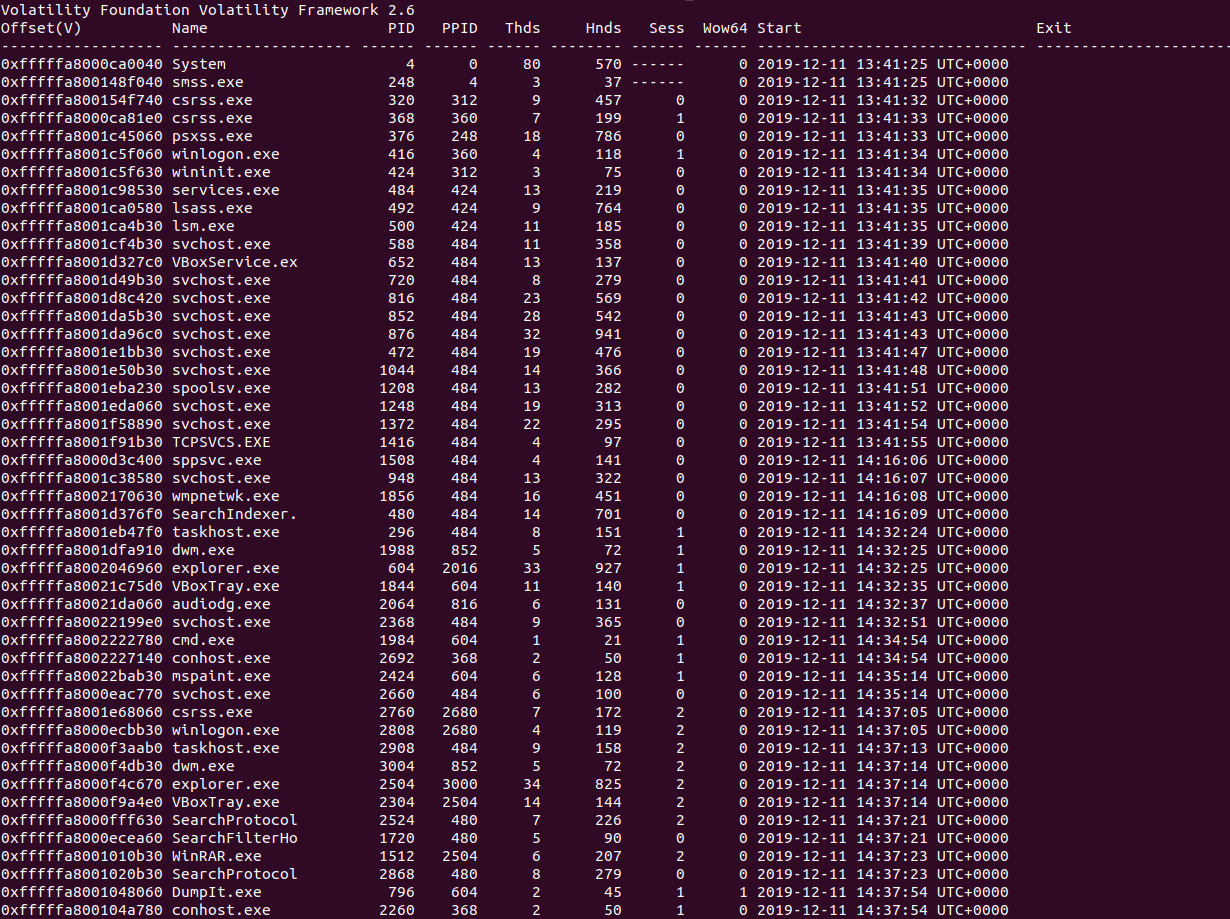
Recently I came across a newly released CTF based around memory forensics, called MemLabs, and as memory forensics is quite an important subtopic in malware analysis, I decided to brush off my Volatility Framework and give it a go!So this is challenge 1 of 6, and I’ll be using Volatility, GHex, and GIMP to complete […]
Happy New Year! It’s been a while since I’ve posted anything here, as I’ve been quite occupied with a few other things – such as the Zero2Hero course that Vitali and I developed alongside SentinelOne, as well as migrating this site from one hosting provider to another, which caused a few issues but should all […]
(This post is a reupload from my old site which is no longer available – you may have seen it before) If you haven’t read the first post, go check it out here. You can download this keylogger off of VirusBay. So far we have decrypted a whole lot of text using a simple XOR method, which […]
(This post is a reupload from my old site which is no longer available – you may have seen it before) Whilst I’m working through the Hancitor write up and the Flare On challenges, I decided to take a short break and focus on a smaller piece of malware – such as a keylogger, which […]